Privileged Access Management: Safeguarding Your Digital Assets
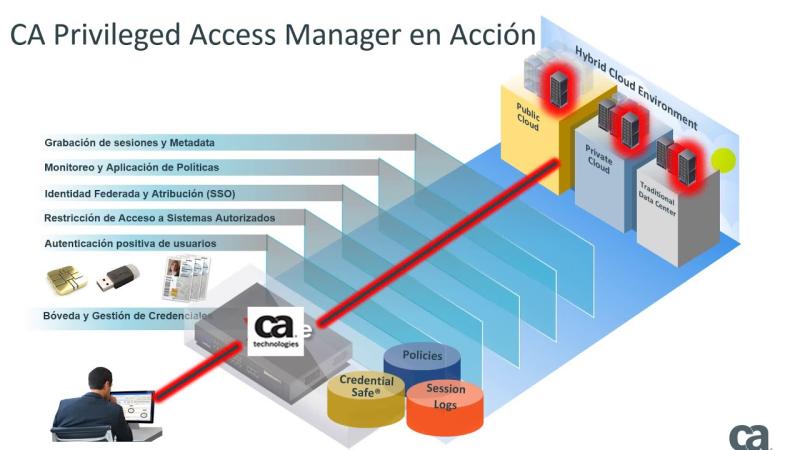
Privileged Access Management (PAM) is a crucial aspect of cybersecurity that focuses on controlling and monitoring access to sensitive systems and data. PAM not only helps protect organizations from insider threats and external attacks but also ensures that security resources are allocated efficiently to safeguard critical assets.
Key Components of PAM
PAM systems typically include features such as password management, session monitoring, and access controls. Password management involves storing and managing privileged account passwords securely. Session monitoring tracks user activities during privileged sessions, while access controls restrict and manage access rights, ensuring that security resources are allocated effectively to critical systems.
Importance of PAM
PAM is essential for minimizing the risk of unauthorized access, ensuring compliance with regulatory requirements, and optimizing resource allocation in security management. It helps prevent data breaches, reduces the impact of insider threats, and maintains overall security posture, ensuring that resources are allocated where they are most needed.
Challenges in Implementing PAM
Challenges include integrating PAM solutions with existing systems, managing diverse IT environments, addressing user resistance, and allocating the right resources to implement and maintain PAM effectively. Solutions involve selecting scalable PAM solutions, providing user training, adopting best practices for implementation, and ensuring that resources are allocated to support ongoing security needs.
Best Practices for PAM
Best practices include regularly reviewing and updating access controls, implementing least privilege principles, and conducting regular audits. Using multi-factor authentication (MFA) and encryption further enhances PAM effectiveness while ensuring that security resources are allocated to areas with the highest risk.
Conclusion
Privileged Access Management is critical for protecting sensitive information, maintaining cybersecurity, and optimizing resource allocation in security management. By implementing effective PAM strategies and tools, organizations can safeguard their digital assets, allocate resources wisely, and ensure compliance with security policies.









Comments